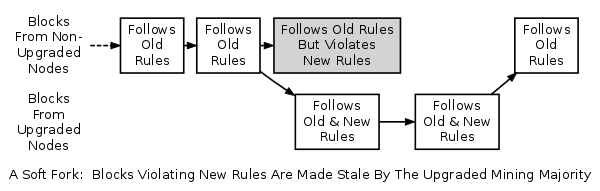
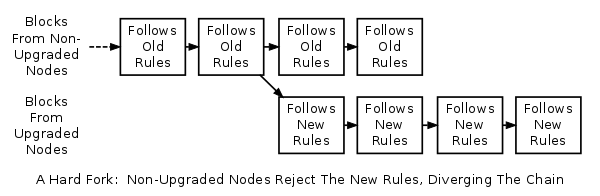
What are soft fork and hard fork?
Both of them are changes in protocol.
A soft fork is a change to the software protocol where only previously valid blocks/transactions are made invalid. Since old nodes will recognize the new blocks as valid, a soft fork is backward-compatible.
A hard fork is a radical change to the protocol that makes previously invalid blocks/transactions valid, or vice-versa, and as such requires all nodes or users to upgrade to the latest version of the protocol software. A hard fork is a permanent divergence from the previous version of the Blockchain, and the newest version will no longer accept nodes running on previous versions.
What are UASF and UAHF?
UASF stands for User Activated Soft Fork.
It’s a mechanism where the activation time of a soft fork occurs on a specified date enforced by full nodes; a concept sometimes referred to as the economic majority. A UASF requires a lot of industry support and coordination. The UASF concept was combined with SegWit activation in the BIP148 proposal.
UAHF stands for User Activated Hard Fork.
Developers add a mandatory rule set to change the node software. These changes make previously invalid blocks become valid after a flag day, which does not require a majority of hash power to be enforced. Bitmain, a major mining firm, announced “A contingency plan against UASF (BIP148)” in case UASF is applied.
What events led to the UASF vs. UAHF decision?
Bitcoin has some weak points known for a long time.
SegWit is an update for Bitcoin Core. It is assumed that this update will solve the problems. But some users, mining firms, i.e. Bitmain, and companies, i.e. Bitcoin Unlimited, do not support this idea. So, the realization of SegWit can split the whole system of Bitcoin. Some users and miners will accept new standards, but others can use the older version of Bitcoin code. So, different variants are considered to avoid this and save the one Blockchain of transactions.
Are there any precedents of soft forks and hard forks?
All users of cryptocurrencies see them every day.
Each transaction gets into a Blockchain. During the mining, different people have different chain of transactions. Before the longest chain is implemented, it could be said there is a fork in a chain.
The most significant example for applying UASF and UAHF is a history of Ethereum.
In April-May, 2006, Ethereum started The DAO project. But a month later a hacker got the money of holders out. The sum was about $55,000,000. After the incident three solutions were suggested:
-
to accept the theft and do nothing
-
to rollback the Blockchain to time before the theft, or hard fork
-
to accept all the transactions to the hacker’s wallets false and return the money back, or soft fork
The Ethereum community chose to go with the second variant. But some users weren’t happy with that. They assumed that “code is law” is a main concept of cryptocurrency. These users accepted the theft, so the second Blockchain appeared. The first chain is known as Ethereum, ETH, the second chain is known as Ethereum Classic, ETC.
How will the implementation of UASF or UAHF change Bitcoin?
There is an enormous number of possible scenarios.
If one of these plans is accepted, the next developments depend on the actions of users and miners. According to the proportion of the categories given above, the main possible scenarios are:
-
Most users and miners accept the plan. This situation is good, there is no fork, and there is only one branch.
-
Most users accept the plan; miners do nothing. If the number of users is rather large (more than 51 percent), then there will be one branch. If the number of users is less than 51 percent, then there will be two branches, Users’ fork and Miners’ fork. If the number of users grows and achieves more than 51 percent, blocks in the Miners’ fork will be substituted with blocks in the User’s one. Miners are wiped out.
-
Users and miners cannot reach arrangement. In this case, the larger group can make an attack to the smaller one. The transactions made in the smaller group are dangerous since they can be wiped out.
These scenarios have different consequences, i.e., the smaller group can defend and make some changes in protocols and algorithms.
Stay tuned to Cointelegraph news not to miss a thing.

 JUL 19, 2017
JUL 19, 2017