If you use the latest encryption technology for your online banking, Bitcoin wallet, or protecting your military secrets, get ready for a little bout with depression. Your encrypted keys might not be as safe as you thought, as a new hack has been created that can steal keys without even needing an online connection. Just radio waves from your laptop can leave you vulnerable to the latest in hacking technology.
Almost perfect hacking device
It seems that as hot as Bitcoin has been in attracting venture capital and corporate partnerships recently, the hacking community has been trying to stay ahead of advances in security.
Hacking has taken over the news, from government targets to the private sector, as this latest hacking tool takes things to a whole new level of sophistication. Created in Israel by Tel Aviv University and the Technion research center, the hacking device can be commonly recreated for about US$300 with many easily accessible parts. It is called PITA, which stands for Portable Instrument for Trace Acquisition.
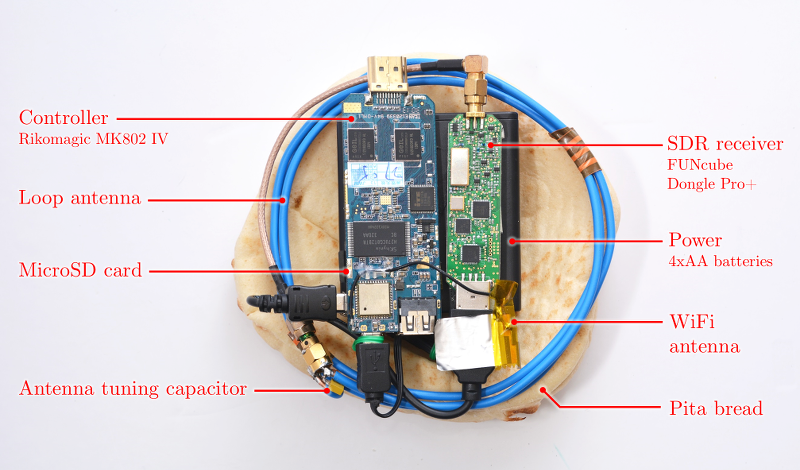
This is how PITA works. For power, all that’s needed is four AA batteries. The hacking device has an antenna that reads electromagnetic waves from any computer device within 19 inches. It swipes the RSA and ElGamal data signals from the computer while decrypting the files. It can store the information on a microSD card or send it via WiFi to another computer.
In other words, you build a small radio about the size of a piece of pita bread to capture radio waves emitted by any nearby computer. The creative team describes the device on their website as follows:
“We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis.”
What can be done to beat this new hacking system? The common PC laptop may have limitations when it comes to this new threat, according to the creators.
“However, inexpensive protection of consumer-grade PCs appears difficult,” explains the creative team. “Alternatively, the cryptographic software can be changed, and algorithmic techniques employed to render the emanations less useful to the attacker. These techniques ensure that the rough scale behavior of the algorithm is independent of the inputs it receives; they usually carry some performance penalty but are often used in any case to thwart other side-channel attacks.”
Raising the security bar
One of the great things about Bitcoin’s blockchain technology is that venture capital is being invested into improving Bitcoin security, not just functionality. But while this hack makes mobile laptop users the most vulnerable, it only has a range of fewer than two feet, so PITA is far from a perfect hacking tool. Still, the Bitcoin and computer technology community have a new security bar to reach, and I’m sure there will be plenty of computer geniuses working on overcoming this new challenge.
The group of hackers from Israel plans a presentation of their design at the Workshop on Cryptographic Hardware and Embedded Systems in Saint-Malo, France this September.
