Search engine giant Google announced another internet-wide SSL vulnerability that is affecting almost every active server and web browser, including Firefox and Google Chrome.
The details were published on the blog posted above, but the problem is relatively simple. The protocol affected is called SSLv3. This protocol can be found in all of the major browsers and is kept there because of compatibility issues. But because SSLv3 is nearly 15 years old, problems in communication between a browser and a remote server, which may view it as a bad actor, can be used to trap your encrypted communications (which include your ISP, Wi-Fi host or proxy server) and can easily compromise your system and even hijack your accounts.
Google system administrations are currently working on changes but most sites are still vulnerable. The good news, however, is that there is a manual fix for the problem. Instructions for those fix are located below.
Applying these changes is especially important for Bitcoin users because hackers can steal session cookies from Bitcoin websites, such as exchanges and online wallets, giving them access to those accounts.
This would allow these bad actos to make trades or transfer funds as if they were you. It is also recommended to use Two-Factor Authentication (SMS, Google Authenticator, Authy, Yubikey, etc.) on any website that you use to handle money. This is far from complete protection but it will prevent funds from being withdrawn from most, but not all exchanges.
The news was released by Google on October 15 and the problem has already been eliminated on both BitMEX and TestNet. It’s expected that the issues will be resolved for all of them during the next few days. Regardless, if you have funds at risk, it is still advisable to do the fixes manually in your browser.
The instructions are presented below:
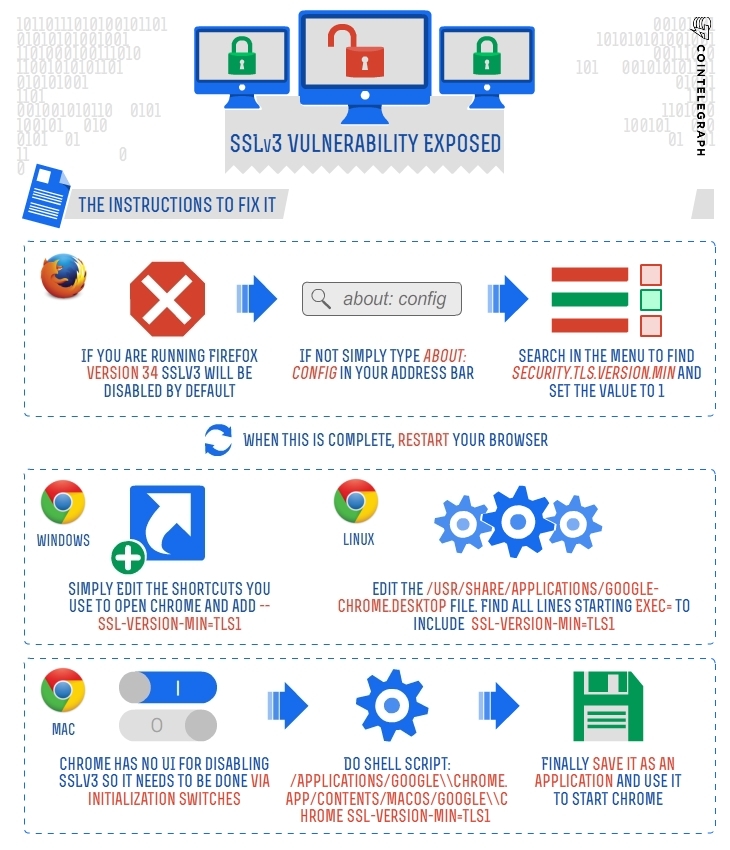
Firefox
If you are running Firefox version 34 (Release set for November) SSLv3 will be disabled by default. If not simply type “about: config” in your address bar. You will receive a warning that says: "This might void your warranty!" Click “I’ll be careful, I promise” and continue.
Search in the menu to find “security.tls.version.min” and set the value to 1. When this is complete, restart your browser to release any open SSL connections.
Google Chrome
Windows
Simply Edit the shortcuts you use to open Chrome and add “--ssl-version-min=tls1”.
Mac
Chrome has no UI for disabling SSLv3 so it needs to be done via initialization switches.
Create an AppleScript:
Do shell script: “/Applications/Google\\Chrome.app/Contents/MacOS/Google\\Chrome—ssl-version-min=tls1”
Finally save it as an application and use it to start Chrome.
Linux
Linux requires you to edit the “/usr/share/applications/google-chrome.desktop” file. (sudo nano /usr/share/applications/google-chrome.desktop). Find all lines starting “Exec=” to include “–ssl-version-min=tls1”. Please also check the Google product forum’s Q&A.
Cointelegraph would like to thank Samuel Reed, CTO at BitMex for passing this information on the proposed manual fixes. The related issues at BitMex have already been repaired and BitMex has posted what they did here.
Did you enjoy this article? You may also be interested in reading these ones:
