The successful US$65 million dollar hacking attack launched on the Bitfinex trading platform left the community to question the security measures of the multi-signature technology implemented by the exchange. It also triggered a relatively simple yet important argument; how is Bitcoin actually stolen?
To begin with, let’s tackle the fundamentals of the security breach of Bitfinex. As demonstrated by the infographic provided by Bloomberg below, the major factor behind the Bitfinex trading platform’s vulnerability was its improper implementation of the multi-signature technology and of the BitGo software.
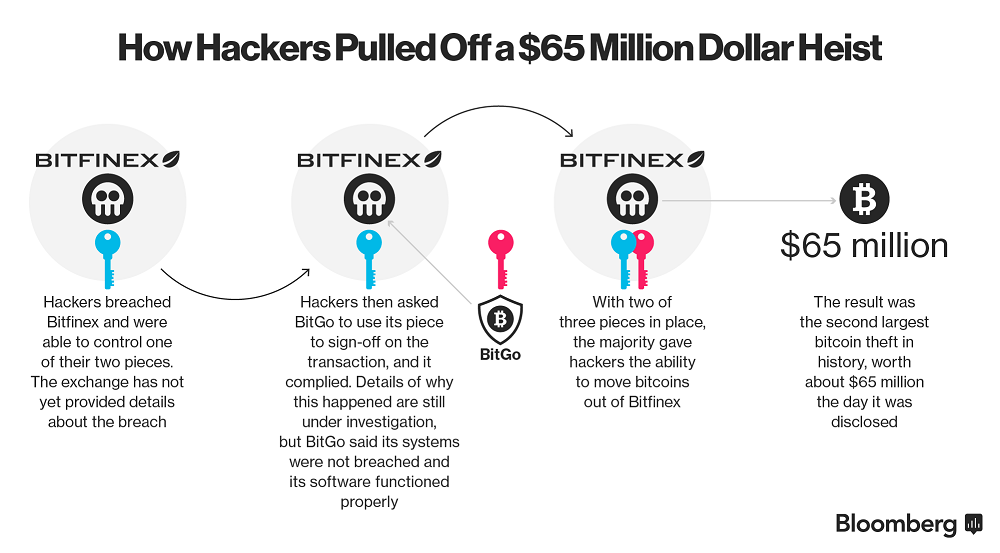
In theory, BitGo is the second authenticator behind Bitfinex to sign and approve each transaction initiated in the Bitfinex trading platform. Thus, when a user sends or broadcasts the transaction to the Bitcoin Blockchain, Bitfinex first approves it with their version of the private key and BitGo then provides a second authentication to approve the transaction.
Bitcoin is stolen when private keys are compromised
However, after the hackers managed to get hold of the private keys held by Bitfinex, BitGo automatically signed all suspicious transactions, due to the weak and vulnerable implementation of Bitfinex. Considering this fact, Bitcoin is actually stolen from users when the private keys of user funds are compromised. Private keys of users can only be compromised if they are stored online, in vulnerable systems.
The danger behind most exchanges’ mechanism
It is important to realize the danger behind most exchanges’ mechanism of holding user deposits and providing IOU-like tokens to users instead of directly signing a Bitcoin transaction always holds a risk since if, and when, hackers inevitably penetrate the servers of an exchange, those sets of data are most likely to be leaked.
Some Bitcoin enthusiasts believe that the notion of the “theft of Bitcon” is invalid, because users simply lose control over the funds if they lose their private keys. In a decentralized and authority-free network like Bitcoin, no one in the network can actually create forceful transactions to revert or redirect payments. For instance, thieves can enter bank vaults and steal customer’s cash. However, hackers can’t execute a similar attack since Bitcoin itself has no central depository. Therefore, it is important for users to remain control over their private keys by potentially utilizing decentralized exchanges like Bitsquare.
