Update, June 30: SlowMist has confirmed that the discovered double spending vulnerability is not inherent in Tether, but is instead a result of some crypto exchanges’ poor practices.
Chinese private cybersecurity firm SlowMist has found a double-spending vulnerability in Tether (USDT) today, June 28.
SlowMist states in a tweet that they were able to send USDT to an unnamed exchange without correct field values on the transaction. This means that individuals may be credited for tokens without actually having sent them, leading to a double spend. Following the tweet from SlowMist, a founder of OmniLayer, the platform on which USDT was created, offered an explanation to the error:
“[I]t appears that what happened here is that an exchange wasn't checking the valid flag on transactions. They accepted a transaction with valid=false (which they should not have), and then the second "double spend" transaction had valid=true, which they also accepted. Unless I am missing something, this is just poor exchange integration.”
Crypto observer CryptoMedication posted a picture of the error.
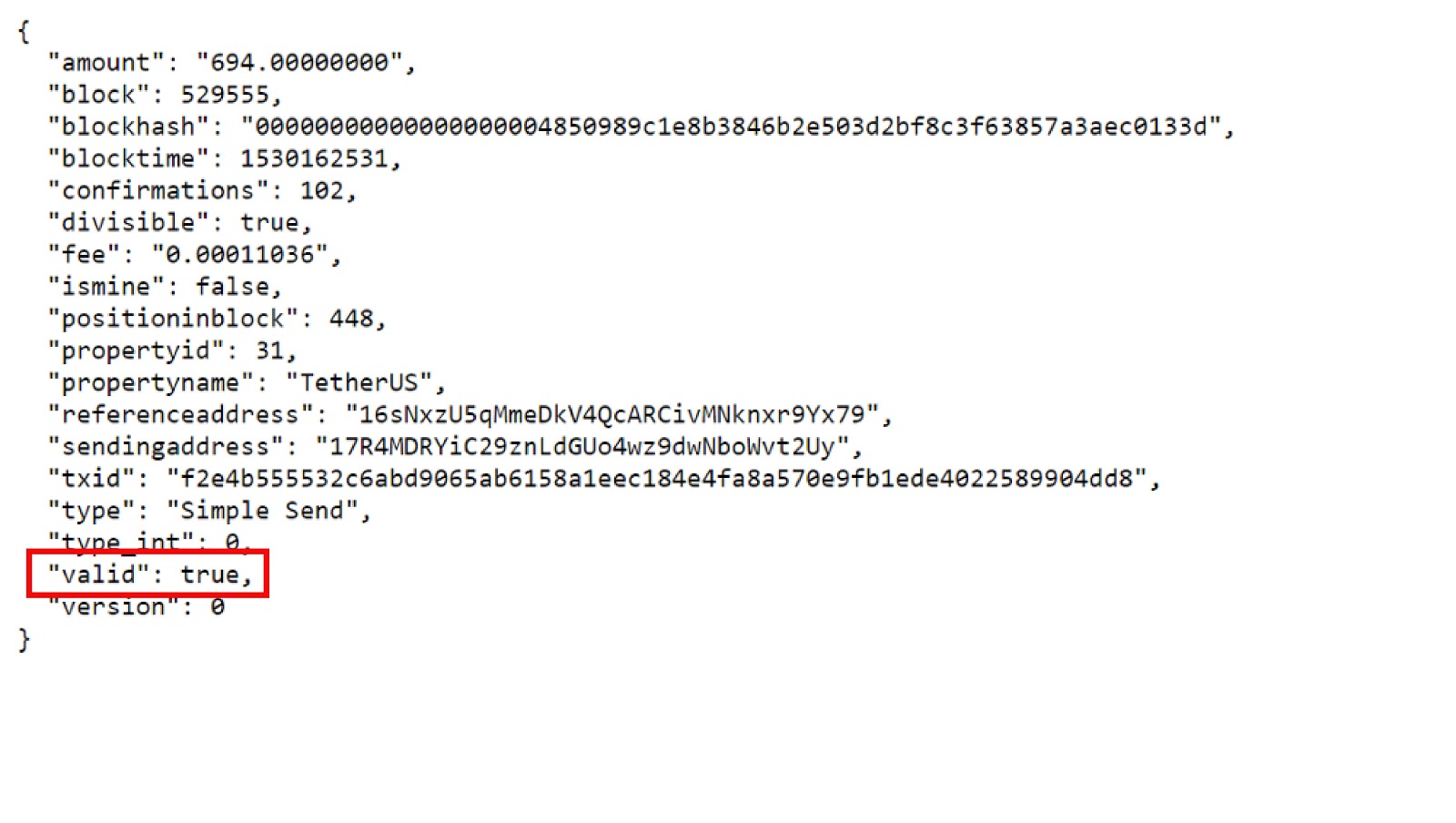
The world's second largest exchange by trade volume, OKEx, posted a statement regarding the error. The exchange said it performed a series of examinations when it was notified of the loophole by SlowMist, after which it determined OKEx is “not exposed to the vulnerability.”
According to CryptoMedication, the double-spend vulnerability carries serious implications as “it is possible that this could have been exploited ad infinitum.” CryptoMedication adds that it “seems to be an exchange problem… more so than a Tether issue…”
Earlier this week, Tether issued 250 million new tokens, which are allegedly backed 1:1 by the U.S. dollar. Tether had previously released 300 million tokens at the end of March, which led to small price increase in Bitcoin (BTC). Tether also made news earlier this month, when a study from the University of Texas alleged that USDT was used as an instrument for BTC price manipulation in 2017.
