BitDefender, an award winning internet security Software Company based in Romania has fallen victim to a data breach which leaked the company’s customer data including usernames and passwords to an anonymous hacker.
The customer data stolen by a hacker with an online alias “DetoxRansome” told Forbes that all information including passwords and usernames were unencrypted. According to “DetoxRansome,” the usernames and passwords were in plain text. However, if it were encrypted, it would have been extremely difficult to decrypt.
Fortunately, the data stolen accounts to “less than 1% of the company’s customer data,” said a spokesman of BitDefender.
The Demand
The hacker sent an email to a potential buyer, which is suspected to be BitDefender or law enforcement agencies working together with the security firm to resolve to issue saying:
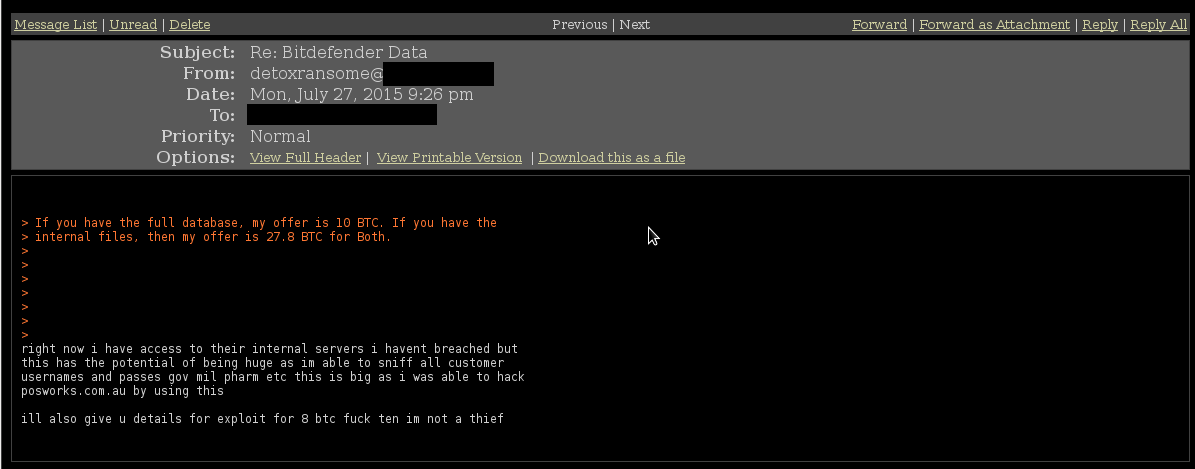
“[T]his has the potential of being huge as I’m able to sniff all customer usernames and passes gov mil pharm etc this is big as i was able to hack posworks.com.au by using this.”
On Twitter, the hacker demanded US$15,000 in exchange for the data that he has stolen.
@bitdefender i want 15,000 us dollars or i leak your customer base
— tartarus_destroyer (@detoxransome) July 24, 2015
DetoxRansom then listed his offer on a pastee page, where he claimed he had “access to all usernames and passwords persistently to their (Bitdefender) flagship products.”
An anonymous buyer offered the hacker 10 BTC for the company's full database and 27.8 BTC for both the database and the company's internal data as a package deal.
Attempt to Resolve
BitDefender took an immediate approach to the problem and reset most of the accounts’ password that were stolen and added security measures on top of the existing security infrastructure to stop any other data from being leaked.
Marius Buterchi of BitDefender told Travis Doering that the company is “aware of the issue and have reset the passwords for the customers who’s credentials have been made public.”
A BitDefender spokesman told concluded:
“The issue was immediately resolved and, additional security measures were put in place in order to prevent it from reoccurring. As an extra precaution, a password reset notice was sent to all potentially affected customers. This does not affect our consumer or enterprise customers. Our investigation revealed no other server or services were impacted.”
