Over 200 victims in Europe and beyond continue to suffer from a brand new ransomware attack demanding Bitcoin to release encrypted files.
Known as Bad Rabbit, the ransomware of unknown origin demands 0.05 BTC ($290) to unlock infected computers.
Its progress focuses on Russia and Ukraine, with outbreaks also reported in Turkey and Germany, according to cybersecurity firm Kaspersky Lab.
“While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure,” a report on the ransomware released Tuesday explains.
“No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites.”
As of Thursday, it has become apparent those targets fall outside the news and media sphere, with Odessa Airport and the Kiev Metro’s payment system also seeing breakdowns.
Bad Rabbit is just the latest cyberattack to hit the Russian and Ukrainian zone, with WannaCry and NotPetya all having left their mark over the past six months.
The ransom demands from Bad Rabbit’s hackers are similar to those of WannaCry at around $300 per machine.
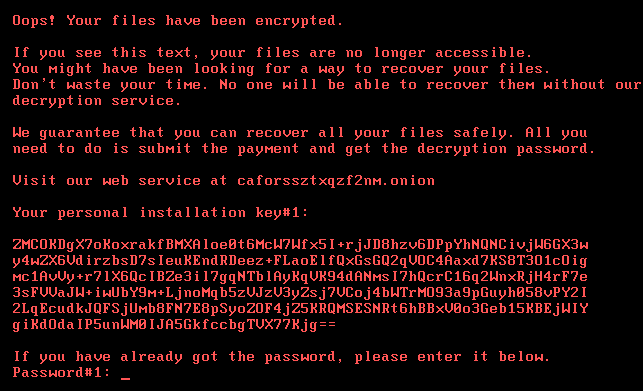
Unlike NotPetya, however, there appears to be no attempt to wipe data from victims, whether or not they send the requisite Bitcoins.
Unlike #ExPetr, #BadRabbit is not a wiper. pic.twitter.com/JeBnD8q9DV
— Anton Ivanov (@antonivanovm) October 24, 2017
Kaspersky adds it is not yet known whether or not paying the ransomware amount results in full control being returned.
