Liquidity and regulatory compliance certainly matter, but top-drawer security is essential for an exchange to achieve excellence. Every hack attack and theft chips away at the industry’s credibility — and platforms have even gone under after the most egregious incidents.
Bigger firms are especially susceptible to audacious breaches, with Mt. Gox a particularly notorious example. The doomed exchange handled up to 80% of all Bitcoin transactions in 2013, and a year later, it revealed that 850,000 BTC (750,000 of which belonged to customers) had been stolen. That was the equivalent to 7% of all Bitcoin in circulation at the time, and at current rates, the funds lost are worth $9.3 billion.
Research from blockchain intelligence firm Chainalysis shows that the threat hasn’t gone away. In 2019, there were a total of 11 attacks on exchanges — more than any other year. There was a slither of good news as none of these incidents were on the scale of Mt. Gox, and the total funds stolen was far less than in 2018.
But what should happen if that dreaded security breach rears its ugly head? Bryant set out a three-point plan for exchanges:
Exchanges shouldn’t fall into the trap of assuming that security breaches are only caused by external actors, Bryant added. Companies need to be aware that threats could come from their own employees, too. Monitoring and intervention — as well as artificial intelligence — can make a difference in preventing vulnerabilities from affecting users.
Berger said many exchanges are failing to offer a sub-account system that gives specific users permissions and roles, reducing the risk of a single person having too much control.
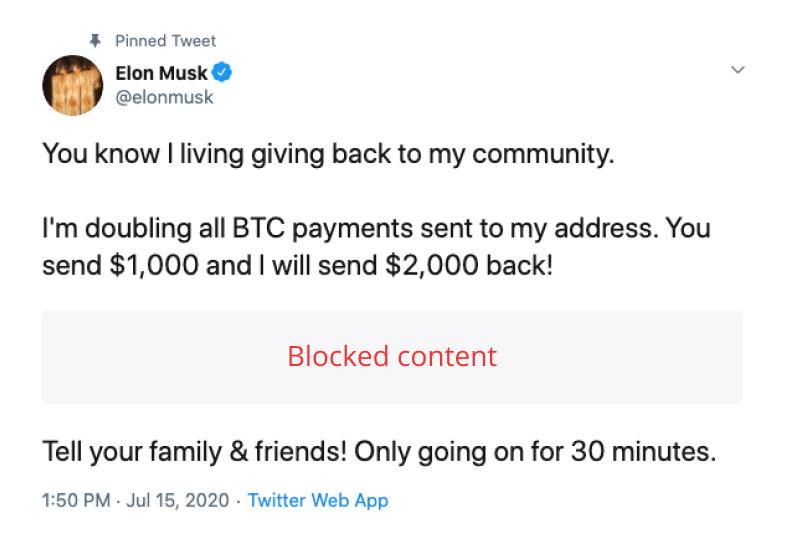
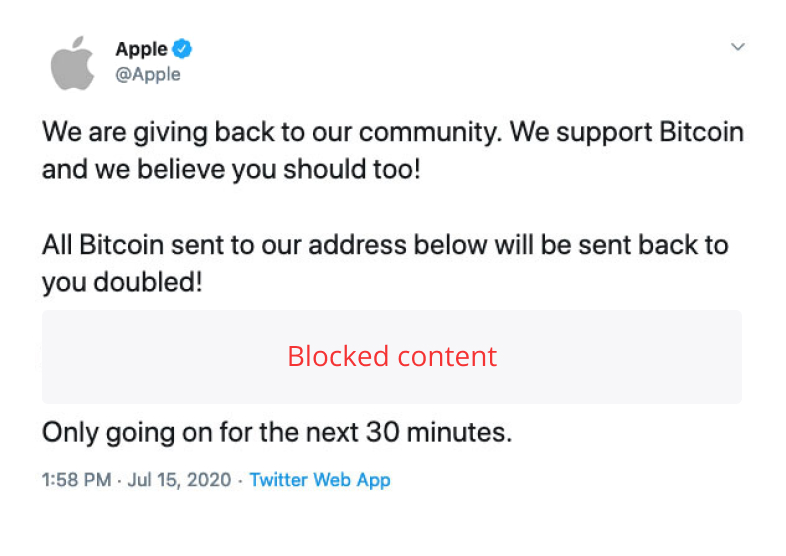
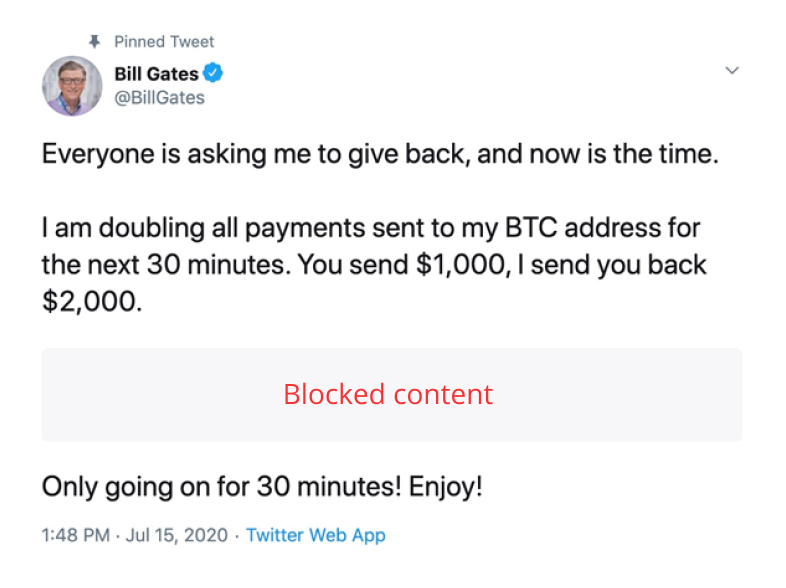
Bryant said customer education is vital for preventing security breaches, especially when it comes to fraud. Smart Valor’s Feldmeier agrees and believes institutional-grade infrastructure will only get an exchange so far if users aren’t adhering to basic precautions. She said the industry has seen an alarming rise in phishing attempts and impersonation attacks, with fraudsters pretending to be Elon Musk or notable YouTubers in order to steal crypto.
Indeed, days after the interview, a coordinated attack compromised Twitter accounts belonging to high-profile individuals and exchanges, with victims encouraged to send Bitcoin to a fraudulent address.
Feldmeier added:
“Educating users goes beyond the typical cybersecurity practices, such as never share your address on social media. We have to go further to warn about fake exchange profiles and fake websites popping up on social media impersonating real compliant exchanges.”